It will be an understatement to label the Internet simply as a groundbreaking milestone in human history. However, like everything else, the drawbacks of this vast connectivity were too apparent and immense to overlook. What’s more, the threat was not limited to a myriad of spam messages or computer viruses. Instead, with time the ways and levels of intrusion in personal space only grew.
The introduction of computer hacking made it easier to access other computers, infiltrate and steal reserved vital information such as bank account credentials, business secrets, identities, etc. With billions of internet-connected devices in numbers that continue to expand, it is only obvious the threat that’s growing along in terms of security of personal space online, sensitive information, data elements, and more. With businesses and government websites being the prime target for the damage.
The following article discusses hacking and ways to protect devices that are the most common target of hackers, such as cell phones, computers, etc.
Contents
- 1 What is hacking?
- 2 How to secure devices and accounts from hacking
- 3 Computers and Laptops
- 4 Use complicated passwords –
- 5 Use a firewall –
- 6 Install anti-virus and anti-spyware software –
- 7 Disable connections when not in use –
- 8 Ignore spam and back up your system –
- 9 Cell phones
- 10 Install a security app –
- 11 Turn off autocomplete and Bluetooth –
- 12 Avoid using unsecured public wifi –
- 13 Use better and strong passwords –
- 14 Online accounts
- 15 Get rid of suspicious mails –
- 16 Use secure devices –
- 17 Beware of the ‘save my info for next time’ feature –
- 18 Let your account alert you –
- 19 What to do if the device or account is already hacked?
- 20 Conclusion
What is hacking?

Much like theft, just online, hackers access websites and devices illegally with the intent to steal people’s personal information and sensitive data. Not just steal, many hackers also alter and delete imperative data leading to crisis.
This data may include anything from your account details, passwords to your conversations and contacts, and even your identity. Since many people bank, shop, and even pay bills online, they are at risk; thus, it is little wonder how all this information reaches online platforms, not to mention the harm a single hacked device can bring about. Moreover, since many hackers are situated outside the US and exercise cutting-edge technology to extract big chunks of information while escaping laws, halting hackers becomes even more challenging.
How to secure devices and accounts from hacking

Depending on the device or the account type in question, one can take several precautions to strengthen their cybersecurity measures ranging from firewalls to software updates and more.
Computers and Laptops
Use complicated passwords –
The first step that anyone can easily bring to action is to set a password that is too complicated to crack. A short password or that with combinations of numbers such as birthdays, etc., can be easily cracked through multiple resources by a hacker.
Do not keep a password with pieces of information that the hacker can trace back to any of your personal information. Also, avoid reusing passwords. A complex password has at least eight characters, a combination of uppercase, lowercase, digits, and symbols.
Use a firewall –

Firewalls are software built with the sole purpose of preventing intrusion into your personal information even when it is connected to a network. What’s more, they even alert a person of any intrusion attempts. While many devices come with a built-in firewall, if your device does not have one, make sure you purchase an efficient firewall depending on the type of network you are connected to. Many companies offer a free trial offer so one can try and decide what works best for them.
Install anti-virus and anti-spyware software –
Viruses, spyware, and malware pose a great threat to the overall security and even functioning of the operating system of your computer and laptops with ad pop-ups, deletion of key files, etc. A good anti-virus software package often has anti-spyware software as well. However, you can also buy them separately as per requirements.
Disable connections when not in use –

Simply shut down the computer or disconnect it from the network when not in use. It not only breaks any connection a hacker might have made with your PC but also makes you an undesirable target for the attack. Being on the network 24/7 makes one more visible to other networks, a perfect target for hacking.
Ignore spam and back up your system –
The need to beware of unknown messages, especially ones with links, cannot be emphasized enough. However, given the changing ways to do the same with messages that mimic the identity of someone you know, it further intensifies the need to take extra care and precautions. Backing your system is a good way to ensure that not everything is lost, even if you fall prey to hacking. An external hard drive backup can make it so you can make up for the data loss and breach without suffering a crisis. Other methods include using two-factor authentication, encryption, virtualization, etc.
Cell phones
Install a security app –

Like firewalls, anti-virus, etc., are for computers, one could also use a security app on a mobile device downloaded from app stores for better security. However, make sure anything you choose to download comes from a trusted source.
Turn off autocomplete and Bluetooth –
Turning off Bluetooth when not in use makes it one less way for hackers to get in. Similarly, autocomplete, a feature that guesses the rest of the sentence as you type, is yet another feature that gives hackers access to your data. So, make sure you turn the autocomplete feature off.
Avoid using unsecured public wifi –

Public wifi connects to your network that many others are using, not to mention how easy and ideal of a target that is for the hackers.
Use better and strong passwords –
Do not give the hackers a chance to guess your passwords. Instead, choose a random combination of numbers that do not relate to your personal information in any way.
Online accounts
Get rid of suspicious mails –

Delete anything that looks the least bit suspicious or spam-like without interacting with it. As for other emails you were not expecting with the identities of someone you know, try contacting the person for the same to confirm it’s theirs before opening them.
Use secure devices –
Do not log into your accounts, social media, or otherwise on any random devices, especially public PC’s which have good chances of being infected with a virus or spyware. Only use your personal device with security measures in place to access anything that another person could use for illicit activity.
Beware of the ‘save my info for next time’ feature –
While the feature to save details given by multiple sites online is helpful, it also makes you vulnerable to any hack on that site. The hacker can easily access the banking credentials and passwords on a site if you choose to save the details on site.
However, if you choose to save it, ensure that the site’s URL begins with HTTPS, where ‘s’ stands for security.
Let your account alert you –
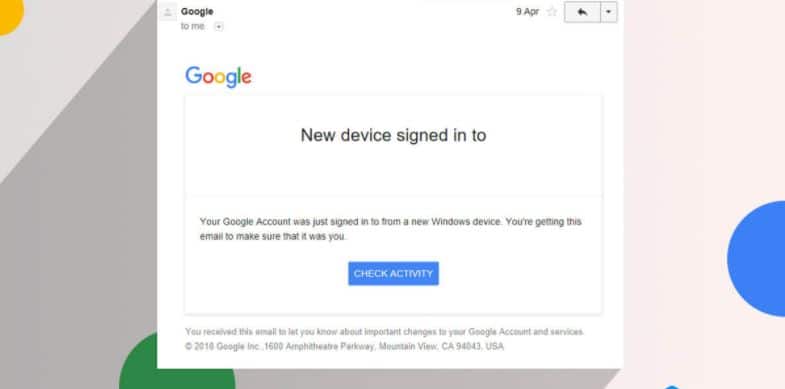
Switching one account alerts is a good way to keep a tab on any unusual activity on the account. The alerts notify a person of any new device which attempts to log in to your account. Upon receiving any such alert, make sure you quickly change your password and deny access to the account.
What to do if the device or account is already hacked?
Despite the efforts, if you find that your account or device has been hacked, make sure to take the following actions without delaying or panicking –
-
- Report hacking and get your devices inspected for the same.
- Change passwords for further protection of personal information.
- Keep an eye on the financial activity on each of your accounts.
- Let your friends and family know about the hack to prevent a chain of damage in terms of personal relationships and future hacks to your contacts.
Conclusion
In recent years, the art of hacking has been increasingly exploited for illicit purposes, and therefore, the need to secure one’s devices and accounts has grown further intense. Making oneself aware of the possibility of hacking, the reasons, and ways out is the first step to a secure connection. One can also take the help of an expert to ensure that their business and website are hack-proof to secure their critical data elements.


